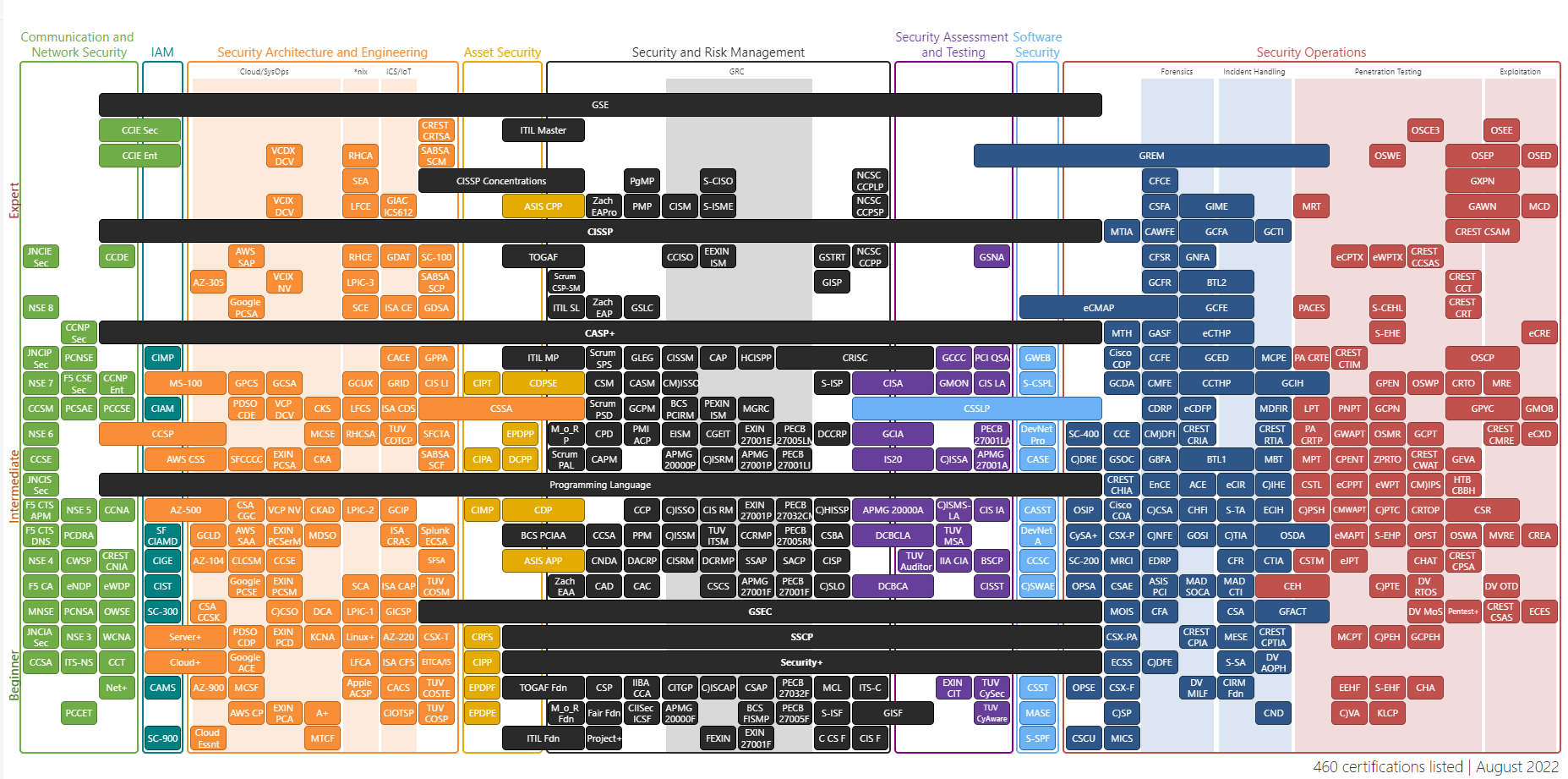
Cybersecurity has become one of the fastest-growing industry as more and more of our personal & professional lives has shifted online. As the industry is growing fast, the demand for skilled security professionals is also increasing.
Obtaining a certificate has become one of the ways to demonstrate one's expertise in this field. Various organisations provide many certifications that will test your expertise in a particular area of security.
Intro to Offensive Security Certified Professional (OSCP)
In this blog, I will share my experience earning a widely recognised and sought-after certification, i.e. OSCP by Offensive Security. Even though it is considered a 'beginner-level certification', you are in great pain if you underestimate it.

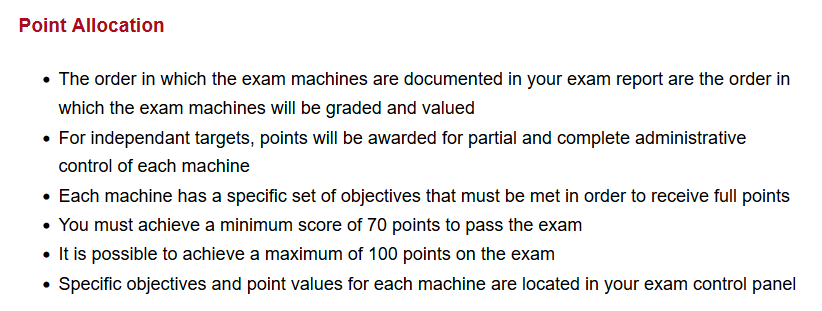
You will need to sit through a 48-hour practical exam to pass the certification exam. In the first 24 hours, you have to search and exploit vulnerabilities on various machines and spend another 24 hours writing a detailed report on how you did those things. Also, did I mention you need to get 70 out of 100 to pass?
Why Should You Pursue OSCP?
OSCP certification is widely recognised and respected in the industry. Even though being certified won't guarantee your employment, it will still open up multiple career opportunities and might even give you an edge in applying for jobs.
For a beginner-level certification, it covers a massive range of topics, from network system security, web application security, buffer overflows, privilege escalation, and pivoting to active directories. As it covers many topics, OSCP certificate holders are often considered to have a complete understanding of information security.
To get certified, you will also need to demonstrate your practical skills rather than answering MCQs and preparing a professional report documenting your findings and recommendations for remediation. This hands-on experience aspect of OSCP sets it apart from other certifications that focus more on theory.
The Exam Preparation Process
I took the exam on December 2nd, 2021 and passed it on my first attempt with 100 points. It was a 7+ months journey full of struggle, all-nighters, and occasional adrenaline rush. Before I started prepping for this certification, I had no prior knowledge of anything related to security, so you might not require as much time as I did. Before I bought the course materials, I spent most of my time going through any free resources I could get my hands on.

By the time I bought the actual course around September, I had gone through almost all the contents on TryHackMe, PortSwigger, some Vulnhubs/HackTheBox, and a few other CTFs platforms. I also completed these courses provided by TCM: Practical Ethical Hacking, Linux Privilege Escalation, and Windows Privilege Escalation.
Course Materials and Lab Experience
I only took one month of lab time, as I had gone through a lot of stuff beforehand and was confident I won't have much trouble with the lab itself. My course officially started on September 12th, 2021, and came with a PDF of over 800 pages and 12+ hours of video materials. I skipped the videos, referred to PDFs when needed, and mostly spent my time reviewing the labs and forum. When my lab time expired, I had gone through 55+ machines.
The Final Stretch
Even though my lab ended in October, I had scheduled my exam for December. I spent the remainder of my time pawning boxes from Offsec Proving Grounds. It is hands down the best and most important resource out there for OSCP. As it is the service provided by the offensive security itself, it even has some retired machines from the exam. I recommend this over other resources, even if it's paid, requiring a $19/month charge.
I also bought the HackTheBox subscription and did about 20+ retired machines, of which most were rated Easy & Medium. My stats on TryHack and HackThebox before the exam are shared below.

The Exam
My exam started at 6:45 AM NPT (UTC/GMT +5:45 hours). I started my exam at around 7:15 AM NPT, as it took time to set up the proctoring software and go through the required procedures before I was allowed to start the exam. Make sure to go through this extensive exam guide by Offensive Security before you sit for the exam.
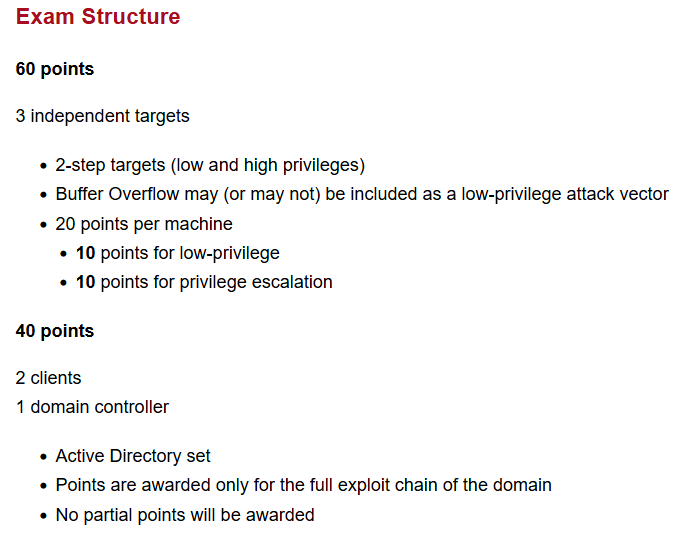
I had secured 50 points on the 4-hour mark but had to spend another 4 just to get that passing mark. Most of the exploits required to gain initial access were web-based. This might not be the same for you, but make sure your web game is strong.
The exam environment also has a lot of rabbit holes designed to waste your time, so prepare a solid enumeration plan and stick with it. Don't be afraid to start from zero anytime, even if you feel like you are close to exploiting certain vulnerabilities.
Privilege Escalation is the easiest part if you know what you are doing. OSCP doesn't demand much in case of escalation, as you don't need to evade AV and stuff. Privilege Escalation courses by Tib3rius and TCM were enough for me, and don't forget to practice a lot. Rely on platforms like HTB and PG for practising.
I started preparing reports right after I got that passing mark, as I didn't want to miss out on any crucial details. Since you can't access the exam environment after 24 hours, I thought it would be better to prepare the report when I had access to it.
By the time I finished my reports, I had scored 80 points and only had 2 hours left before my access to the exam environment expired. I returned to the environment to earn that sweet bragging right of getting 100 points. Solved the last machine, updated the report, and submitted it. Three days after submitting my report, I got a mail saying I had passed the exam.
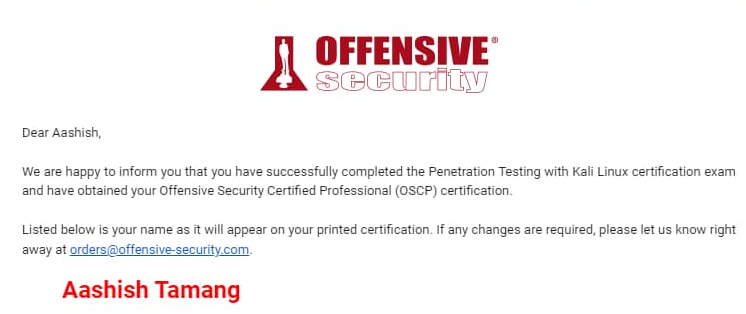
After all the struggle, countless all-nighters, and constant brain abuse for 7+ months receiving this mail marked the end of the OSCP journey for me. This article might not be the one you were searching for, as I merely shared my experience. In the next article, I will share my knowledge and essential resources that helped me ace the examination, so stay tuned!
Comment below if you have questions, and subscribe using either of the buttons below.
