Hardening in Security
Operating systems evolve and add more features to make things convenient for their users, so it is essential to optimize their security settings as more features mean more exposure to cyber security threats.
In security, hardening is securing a system by applying best practices according to the different security models, limiting features and services allowed to run in a system, implementing proper access controls, etc.
Some ways to harden your Windows 10 machines are:
Clean Installation
The most important thing is to ensure that you use an official image of whichever operating system you try to install. Official sites often have hash values listed, so you can compare the hash of the downloaded ISO (or anything) to ensure the files are not corrupted or modified.
If you bought the used PC, it is strongly recommended that you wipe everything and clean and install a new operating system so that any malware, viruses, or bloatware are removed from the system.
Enable Auto Updates
Windows gets minor patches and updates monthly, consisting of that month's security and reliability updates and the previously released updates. Ensure that you have enabled auto-update, and the PC will have internet access during the update.
Even if you have enabled auto-update, manually check for updates periodically so that you don't miss out on any important security updates that may compromise your system's security.
Application Management
Even a clean installation of any operating system includes bloatware or unwanted programs. You can check system installed apps by going to Settings > Apps ( Apps & Features). Check all the installed programs and uninstall the ones you think will not be used.
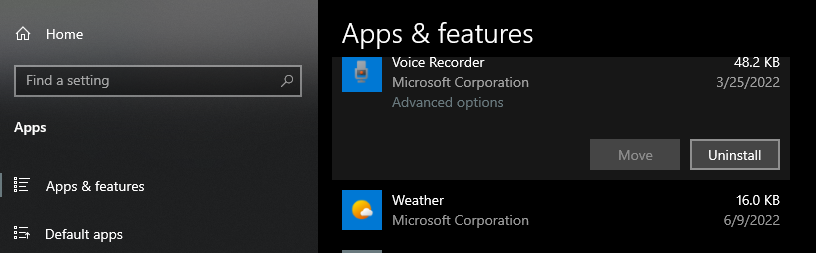
Uninstalling unwanted applications isn't enough, though. You might want to install various applications required for work or personal reasons. Always download those applications from their official site and compare the hash of the downloaded application with the one listed on the site.
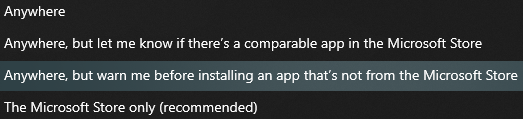
Configure Windows only to allow the installation of approved applications from well-known software repositories (Microsoft Store). You can configure this by going to Settings > Apps and choosing the recommended option.
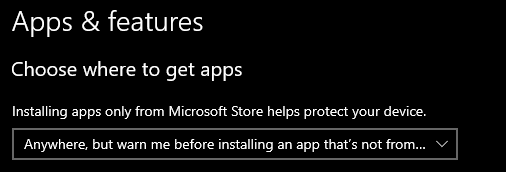
If your work needs software and applications unavailable in the Microsoft Store, choose the 3rd option. Again, ensure that you download the application from their official site.
And last but not the least, check for updates periodically. Even better if the application has an auto-update feature. New vulnerabilities are reported and fixed daily, so you must install and apply those patches as soon as possible.
Disable Unwanted Features and Services
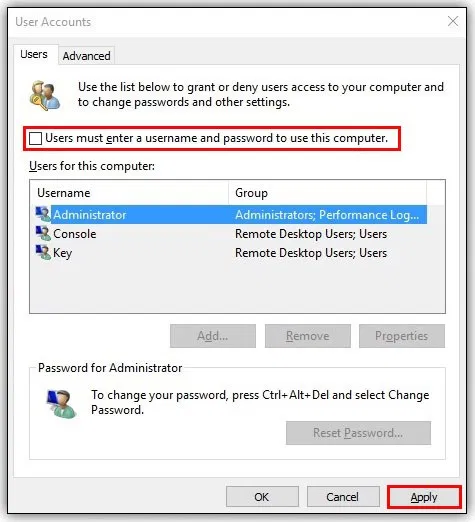
Some features like automatic login are enabled by default. It is a very dangerous feature as anyone with access to your PC will be able to log in without any credentials whatsoever. To disable this feature, press Ctrl + R then enter netplwiz and check the box and click apply.
Remote Access is another feature malicious attackers use to gain control over your system. It is disabled by default, but in case you enabled it, you can simply disable it by going to Settings > System > Remote Desktop and check "Don't allow Remove Connections".
If you have SSH, FTP, or HTTP running, then ensure you have configured them securely. Do not allow access to any of them without proper authentication; once you are done using them, it's better to disable them. Remember, the less your services are exposed, the less vulnerable you are.
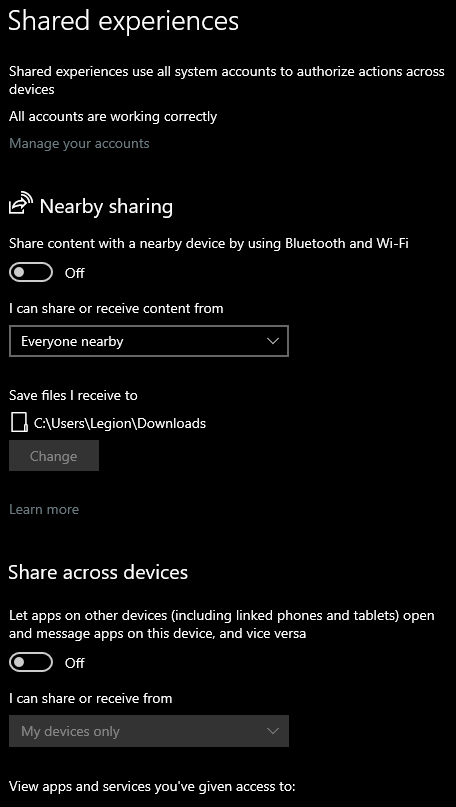
Turn off Bluetooth and other sharing features when you are not using it. Windows has a feature called Nearby sharing. Make sure to disable it if you are not using it.
Encrypt Your Data
Windows has a built-in proprietary disk encryption software, i.e. Bitlocker. It is free, and you don't have to install any third-party software. Once you encrypt your data with a strong password, it is protected from unauthorized access and prevents unauthorized changes.
Turning on Bitlocker is very easy. You simply right-click the drive you want to lock and select "Turn on Bitlocker".
Set up Password Managers
Instead of storing passwords in text files or browser safe or using the same password for everything, install a proper password manager application to make your life easier.
Password managers can generate strong passwords and store them for you, so you don't have to remember them. Some well-known password managers are Lastpass, Keeper, Bitwarden etc.
Setup Backups
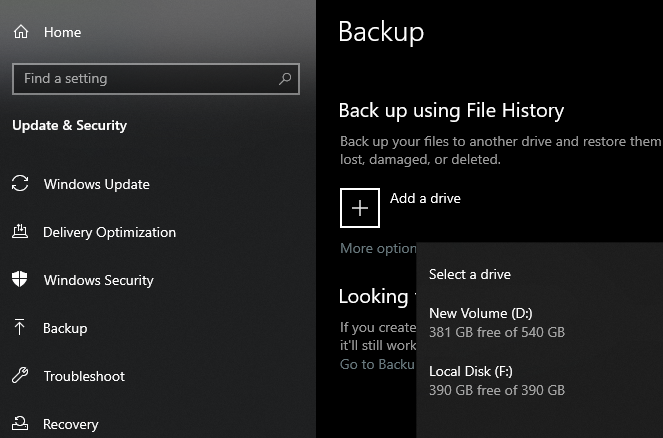
Backing up important files is very important. You don't want to lose your files if something happens to your PC. Windows 10 has a built-in backup feature called File History, which you can turn configure by going to Settings > Update & Security > Backup.
You can simply insert an external hard drive and use it as an external backup. You can configure how often you want the files to be backed up and how long should the drive keep the backups (and delete older ones automatically).
Miscellaneous
Secure Authentication
Along with a strong password, you can set up Multiple Factor Authentication to block any unauthorized access in case your password is compromised. It is also possible to go passwordless entirely as you can use something like a hardware security key or biometric login.
Fido2 by Yubico is one of the best security keys supporting NFC, Biometric, and various port supports.
User Accounts Management
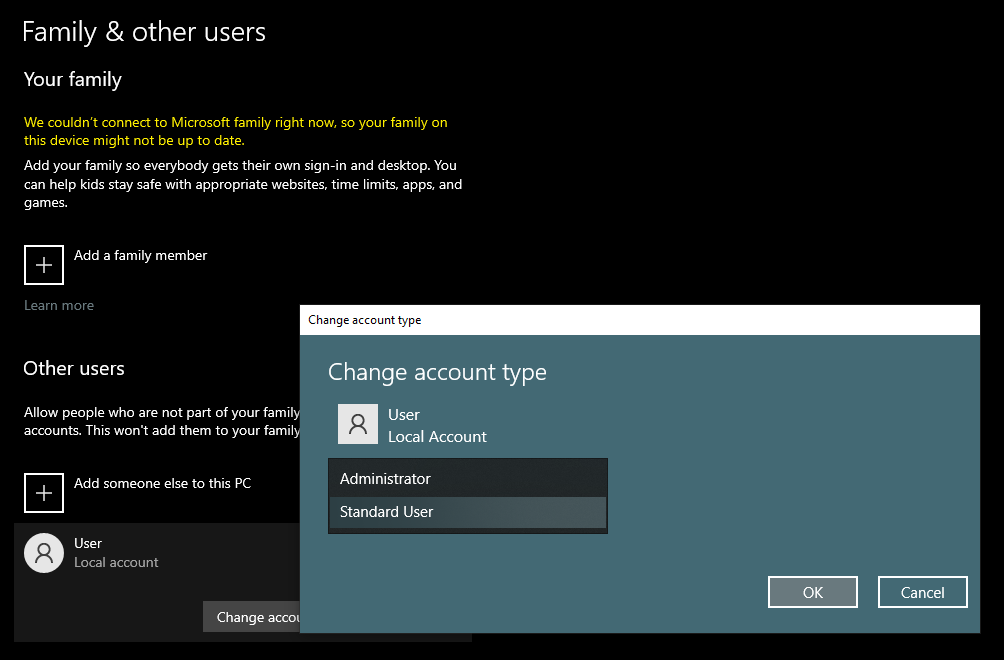
By default, the account you created is assigned an administrator role. Administrators can do anything on your system. If your administrator account is compromised, you give the attacker full access to your system. You also do not need to be an administrator to do some basic stuff unless you want to install a new program or make changes to protected files.
So, it's better just to create a local account without many privileges assigned to it so that even if the account is compromised attacker won't be able to much to harm your system. You can create a new standard account by going to Settings > Accounts > Family & Other Users.
Disable Powershell
Powershell is a powerful tool that can be used to do some advanced configuration, manage various windows features, install applications, automate tasks, etc. As its a powerful tool, it can be misused by attackers to achieve various things.
If you don't know what PowerShell is and don't need to use PowerShell, it is recommended to disable it.
Turn on Ransomware Protection
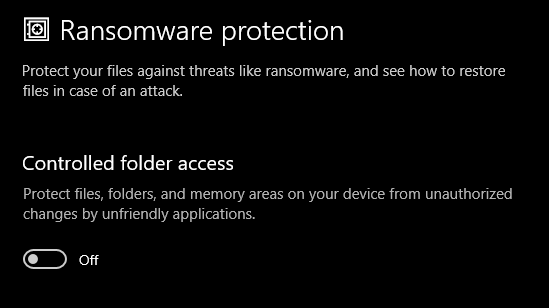
You can prevent applications from making unwanted changes to your files and helps you restore your original files in case of ransomware attacks. Simply search for "Ransomware Protection" to enable and configure it. You can specify which folder and files to protect and which folders to exclude.
Turn on Built-in Guards
These built-in security features are enabled by default. But in case it's not, make sure to enable them. They can be configured from Virus and Threat protection settings.
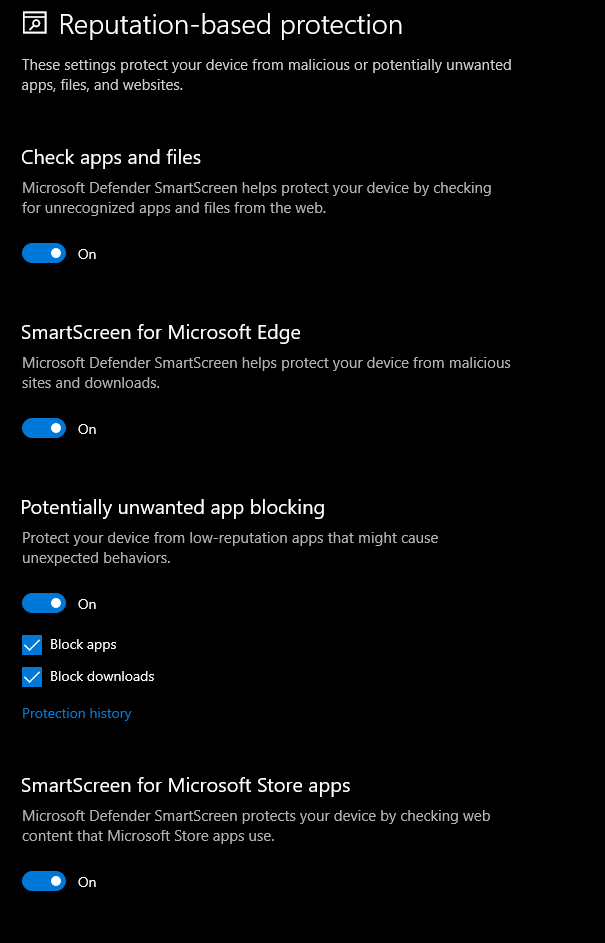
These are some ways to configure your machine to harden your security. Stay tuned for more!
