While the Google Play Store contains almost every android application you will need, it does have its limitations. You might find an excellent app with better features and is well maintained than the counterparts in the Play store. Installing them is easy, as Android allows users to install an application from third-party services by default. But doing so is very risky and might not be worth the risk.
Play Store apps are often safer, as they have to undergo a different testing phase before they are available to download. While some dangerous apps do get through the vetting process, they are removed immediately once deemed harmful.
While on the other hand, applications hosted on third-party stores, Github, and other sources don't go through the same checks. They aren't regulated, and you are just hoping the developers have not included anything dangerous.
In this article, we will talk about the consequences of installing APKs from unknown sources.
How an APK becomes Malicious
APKs themselves are not malicious files. They become dangerous when a malicious actor decides to insert malicious code into the Android apps. There are thousands of variations of trojan, malware, etc., available which can be used for different purposes. One of them is AndroRAT.
AndroRAT is a well-known trojan which injects Remote Access Tool (RAT) into a carrier app. When an app with AndroRAT is installed onto a device, the attacker can remotely control such device. Since it injects itself into a carrier app, the attacker can make calls and send messages from the infected device, among other things.


Attacker's Action in an Infected Device
These applications hide among the legit applications and are often hard to spot for an unsuspecting eye. Different malicious trojans serve different malicious purposes. While some may take a bunch of your phone resources to mine stuff (while making your device a hot mess), others may encrypt everything in your device, making your device foreign. Here are some things an attacker can do when an application with AndroRat is installed.
Getting device info
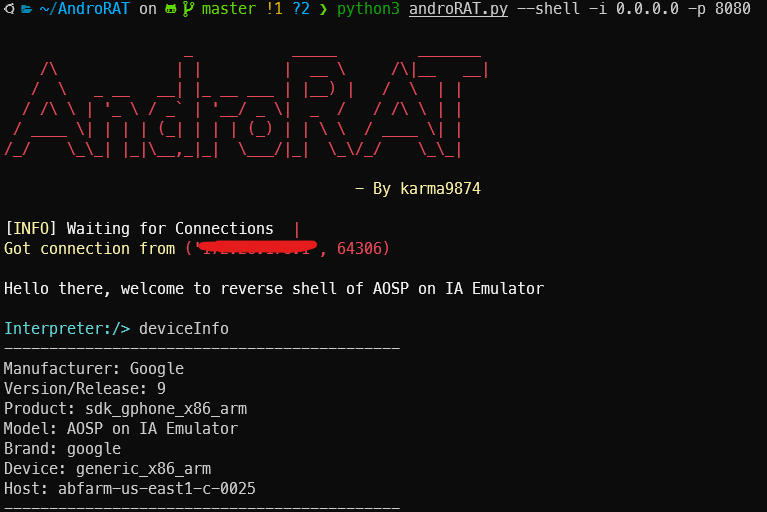
Getting your device info is as easy as it gets. Using one command, the attacker will access all the information about your device IMEI, MODEL, BRAND, etc., without raising any suspicions.
Record videos and capture images using your phone
Attackers will even have access to your cameras. They will take your photo, and you won't even know about that. They can start recording you when you are not expecting it. This is very dangerous as attackers can capture you at your vulnerable point and use it for various wicked purposes.
Record audio using your microphone
Everything you talk about is no longer private, even when alone. How scary is that? Once your device is infected, the attacker can start recording audio at their will.
Get call logs and SMS logs
Call and SMS logs as well? Yes. This is one of the most dangerous things a trojan can do. Your messages will often contain a lot of personal and sensitive messages. Bank details, OTP, 2FA codes etc. Attackers might even be able to get access to your online presence because of this.
What More Can These Applications Do?
These apps can do basically everything. Depending on what purpose they were made. As I mentioned, each malicious app is tailor-made for certain use cases to increase its effectiveness.
For example, applications containing Joker malware can intercept OTPs and security codes, read notifications, make calls, etc.
Recently, the game disguised as the mobile version of CYBERPUNK 2077 was ransomware. Once the game was installed, it would encrypt all the files in your device and ask for bitcoins as ransom.
Some applications contain trojans that blast ads on your device, download stuffs from the internet without your knowledge, and use your device for crypto mining, making your device hot and slow.
What Should You Do to Be Safe?
First of all, avoid installing any applications from unknown sources. You might be tempted to download a crack of some popular applications, but ask yourself if it is worth the risk of compromising your security.
Disable the 'Allow installation from unknown sources' feature from your device settings. Do not click on any unknown links, even if it was shared by your close friends and family.
Even knowing all the dangers, if you still want to install the application, the least you can do to stay safe is scan the APK using anti-virus or malware solutions first. Use a burner phone that doesn't contain sensitive information and won't affect you even if it gets compromised.
That's all, and you can click on the buttons below to subscribe to us and get these articles as quickly as possible!
