CIA stands for Confidentiality, Integrity, and Availability. Although it shares the abbreviation with a certain popular government agency, this CIA has nothing to do with that one.
The CIA triad is a model widely accepted in information security that guides an organisation's policies to keep data, networks, and devices safe and secure.
This article will briefly talk about the 3 components of the CIA Triad – Confidentiality, Integrity, and Availability.
C - Confidentiality
Ensuring confidentiality means preventing the disclosure of sensitive data to an unauthorised access attempt. A key component of maintaining confidentiality is to check that only authorised people have access to specific assets.
Some of the methods used to achieve confidentiality are briefly discussed below.
Encryption
Encryption is the process of scrambling data to make it unreadable using one or more mathematical techniques, also known as cryptographic keys. Data can be encrypted using two main encryption methods, i.e. Symmetric and Asymmetric.
In symmetric encryption, the data is encrypted and decrypted using the same key, while in asymmetric encryption, a pair of private and public keys are used. Data is encrypted with a public key, and the private key is used for decryption.
Some common encryption algorithms are:
Symmetric
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- Blowfish
Asymmetric
- RSA (Rives Shamir Adleman)
- Diffie-Hellman
- ECC (Elliptical Curve Cryptography)
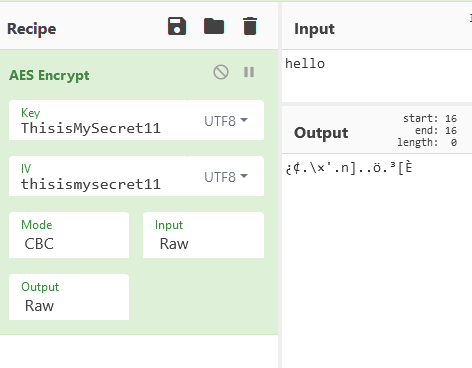
Encrypting sensitive data such as PII, documents, contracts, etc. helps to maintain confidentiality, as even if an outsider was somehow able to get data, all they see is a collection of jumbled words and letters which don't make any sense without the decryption key (see image below for reference).
Access Controls
One of the fundamental components of achieving confidentiality is access control. We can guarantee that users are who they say they are and that they have the appropriate permissions to access certain data through access control.
The key elements of access control are:
- Identification & Authentication: Identification is a person claiming their identity through various means such as username, ID, and email. Authentication is user proving their identity using a password, fingerprints, PIN, etc.
- Authorisation: Access to resources should be granted or restricted depending on the role and responsibilities of the person requesting access. Proper authorisation ensures that users have all the permissions required to fulfil their responsibilities while restricting access to data outside their authority. For example, an accountant will need access to the documents related to an organisation's finances but might not need the documents related to management.
I - Integrity
Ensuring data integrity means providing assurance that the data has not been tampered with and can be trusted. Integrity deals with detecting whether any unauthorised modification has occurred accidentally (hardware, software, or human errors) or deliberately (malicious actors, unauthorised users).
Some of the ways to provide integrity are below:
Hashing
Hashing is the process that translates the data or information into a value, also known as a hash, using a mathematical algorithm. Unlike encryption, it's a one-way process, and the hash cannot be traced back to its original value.
Hashing possesses a property called the avalanche effect, where the resulting hash of data will change drastically if the input is tampered with. So, two hashes can be compared (of the original file and its copy) to see if a copy of the file does not match the original. Some popular hashing algorithms are MD5, SHA, and NTLM.
Certificates and Digital Signatures
Certificates are digital documents that prove the identity of an individual or organisation. They generally include the public key and information on the certificate's owner. A digital signature prevents an unauthorised person from impersonating the sender, thus maintaining the integrity of the data.
A - Availability
Data and information are only useful if they can be accessed whenever required. If the data and services are not available at crucial times, then the purpose of such data and services is lost. Some data and services might need to be up 24/7 for 365 days, while some might just need to be available during work hours, depending upon the organisation and nature of the service.
Redundancy and Fault Tolerance
Any system, hardware, and software will fail eventually. Even if you don't know when and how they will fail, you need to be prepared for that eventual crisis. Redundancy is the duplication of data and services so that the system doesn't have a Single Point of Failure. Therefore, a backup will be up and running even if there are one or two hardware failures. For the users, it feels like a fault never even occurred.
Some of the ways to achieve redundancies are:
- Disk redundancies: The use of technology such as RAID provides fault tolerance in case one or more disk fails, depending on the RAID configuration.
- Load Balancing: Using multiple servers to support a single service can increase the availability of crucial services.
- Backups: Data can be corrupt, lost, or deleted due to hardware or human errors. So, a backup is necessary to prevent data loss in unforeseen incidents.
Hope this information was useful to you. Stay tuned for more articles relating to security!
